Offboard device from Microsoft Defender for Endpoint
Offboard device from Microsoft Defender for Endpoint using Mobile Device Management tools
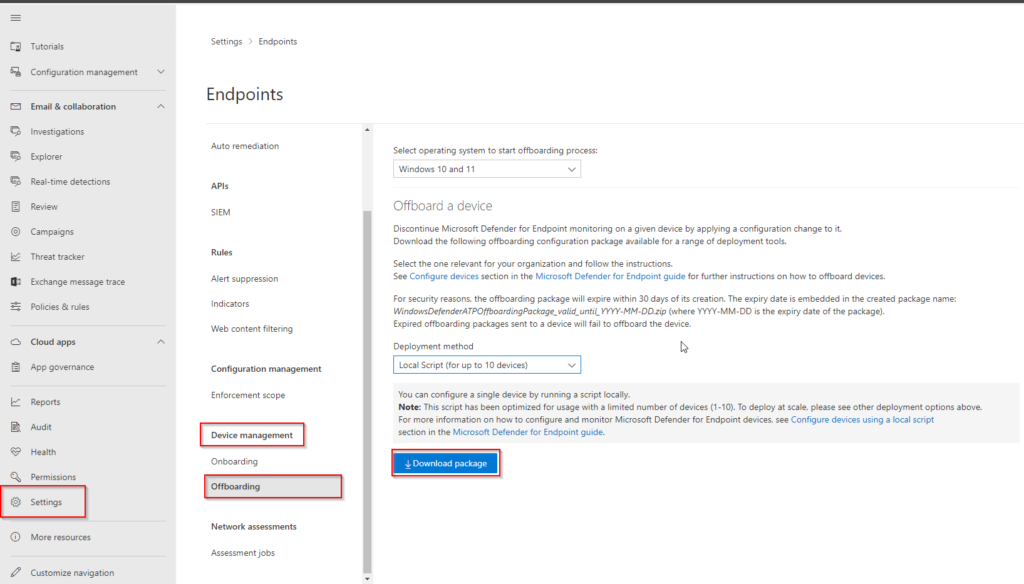
- Get the offboarding packet from Microsoft 365 Defender portal
- Navigate to Settings => Endpoints => Device management => Offboarding
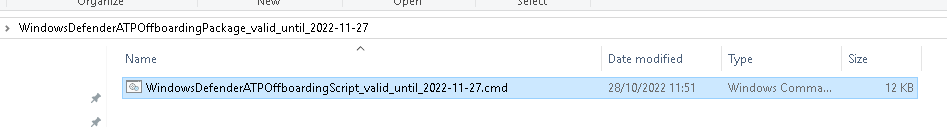
- Extract the script on the client
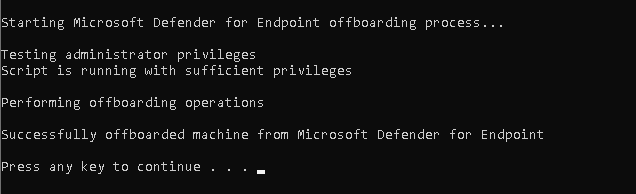
- Run the script as administrator
Resources:
Offboard devices from the Microsoft Defender for Endpoint service | Microsoft Learn
Onboard Windows devices to Defender for Endpoint using Intune | Microsoft Learn